2-Daml sample
Daml ledger, Canton
https://docs.daml.com/canton/usermanual/installation.html
get start sample
https://docs.daml.com/getting-started/index.html
version 1.18 can run DAML without Canton.
But latest version need Canton.
Key Architectural Concepts in Daml
Daml comprises two layers necessary for building multi-party applications: the Daml smart contract language and the Canton blockchain and protocol.
The Daml language is a smart contract language for multi-party applications. Conceptually, Daml is similar to the Structured Query Language (SQL) used in traditional database systems, describing the data schema and rules for manipulating the data.
The Daml language:
defines the shared state between the parties, including process permissions and data ownershipdefines workflows, execution policies, and read/write permissionsenables developers to build rich transactions that codify strict business rulesdefines the APIs through which multi-party applications can talk to each other and compose
The Daml code that collectively makes up the data schema and rules for an application is called a Daml model. Increasingly sophisticated and valuable solutions are composed from existing Daml models, enabling a rich ecosystem that accelerates application development.
Using the Daml language, developers define the schema for a virtual shared system of record (VSSR). A VSSR is the combined data from all parties involved in the application. The Canton protocol ensures that each party gets a unique view into the VSSR, which is their projection of the full system.
In the execution model for Canton, each party of the application is hosted on a Participant Node (Diagram 1). The Participant Node stores the party’s unique projection and history of the shared system of record. Participant Nodes synchronize by running a consensus protocol (the Canton Protocol) between them. The protocol is executed by sending encrypted messages through Domains, which route messages and offer guaranteed delivery and order consistency. Domains are also units of access control and availability, meaning an application can be additionally protected from interference by other applications or malicious actors by synchronizing it only through a given domain, and restricting which participants can connect to it.
Diagram 1:
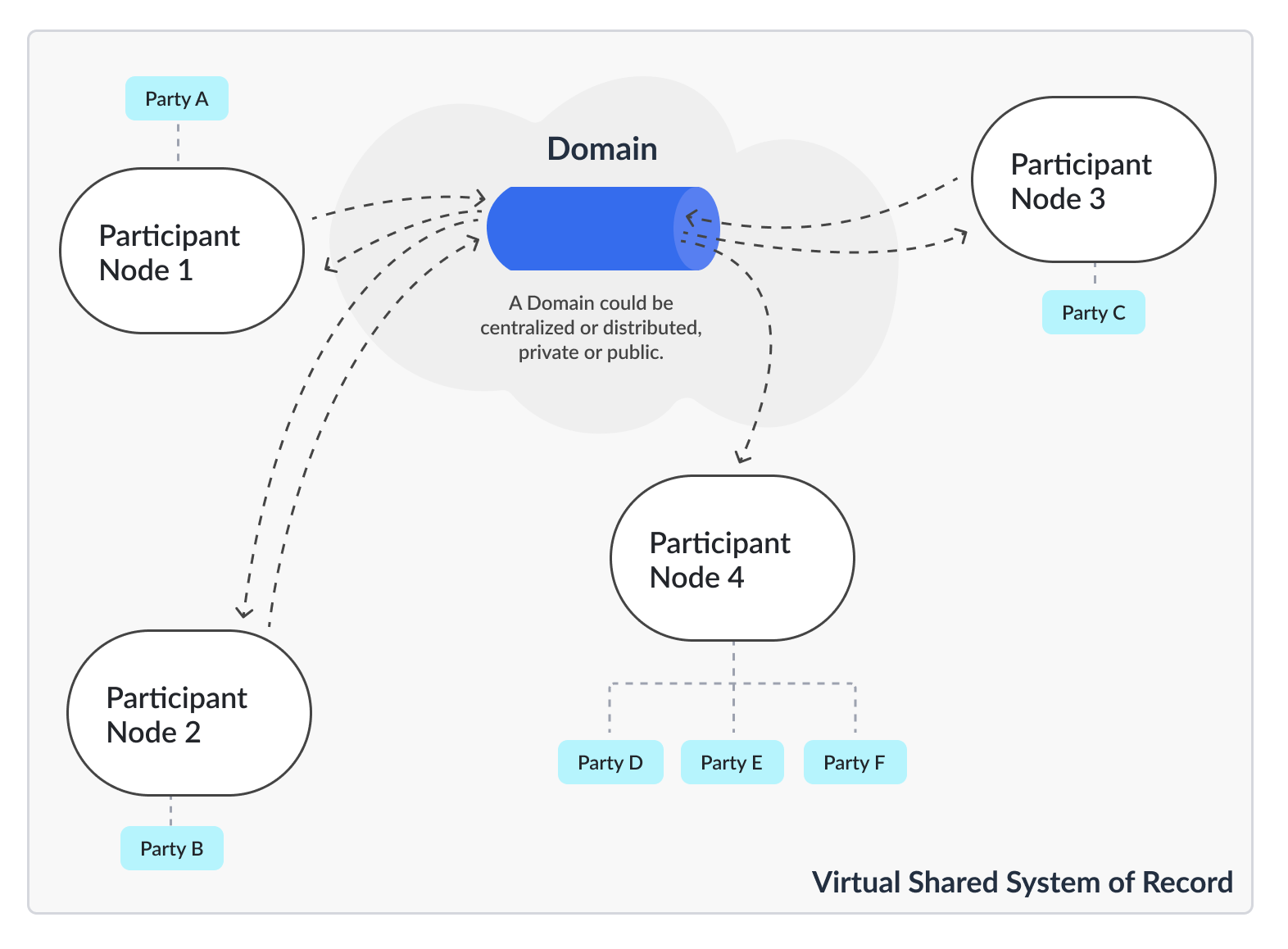
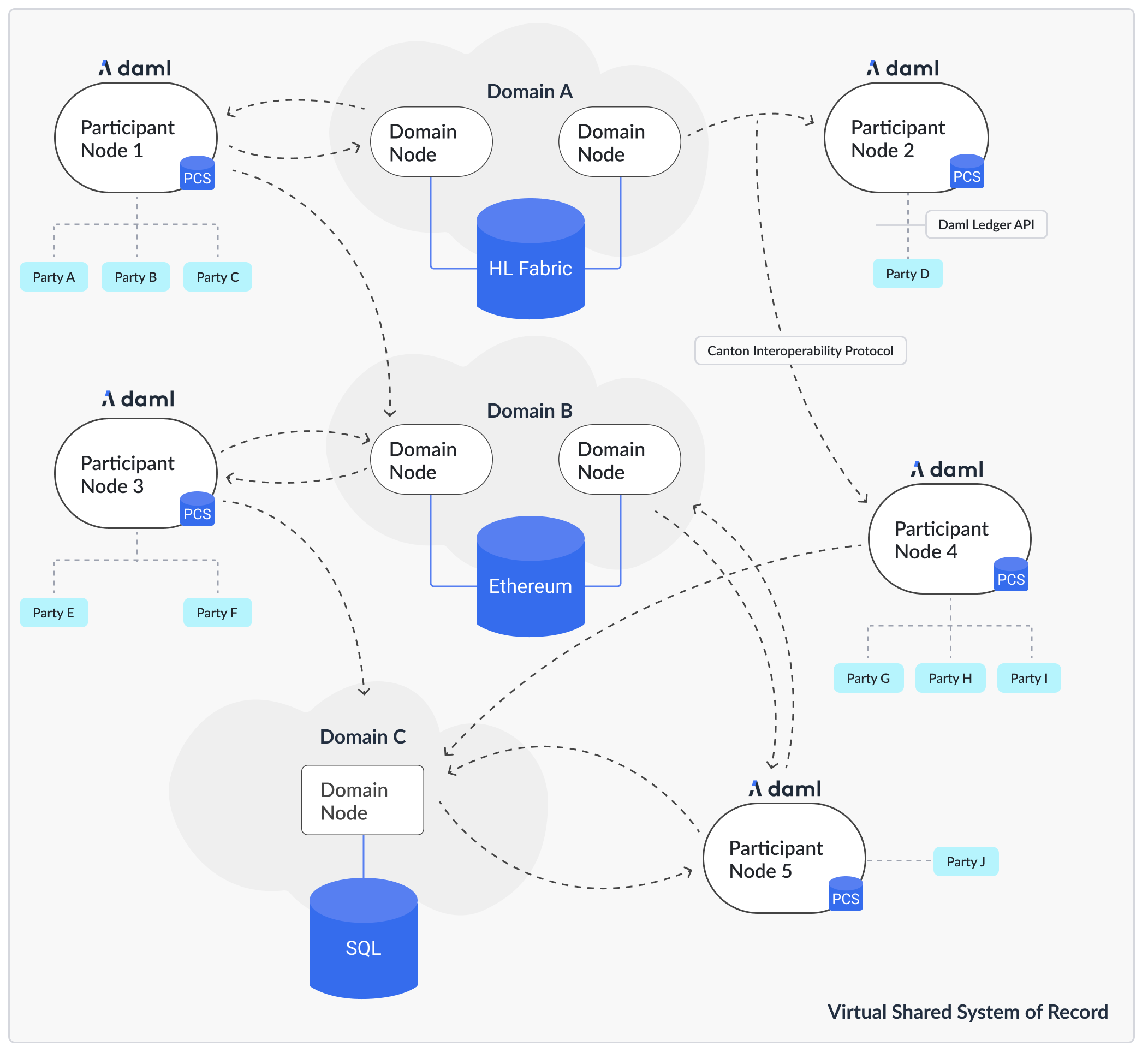
In a composed solution, each domain is a sub-network. A Participant Node connects to one or more Domains, enabling transactions that span Domains (Diagram 2).
Diagram 2:
Transfer Example Using Daml
Consider the transfer example described above with Alice and Bob. Using Daml, the process looks like this:
- Alice logs into her online banking at Bank A and enters a transfer to Bob at Bank B.
- The online banking backend creates a transaction that deducts $100 from Alice’s account and creates a transfer to Bob at Bank B.
- When Bank B accepts the transfer, Bank A credits $100 to Bank B’s account at Bank A and Bank B simultaneously credits Bob’s account by $100.
- Bob’s online banking interfaces with the Daml Ledger and can see the incoming funds in real time.
At every point, ownership of the $100 is completely clear and all systems are fully consistent.